The Petya variant encrypts the MBR and rest of the hard disk drive, then attempts an operation similar to WannaCry. It displays a message informing victims that their files have been encrypted and that they should send $300 in bitcoin to a specific address to decrypt their files.
First Published 30th June 2017
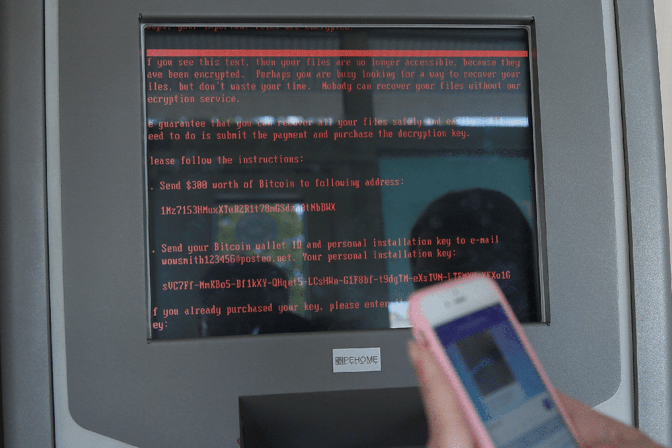
All your data are belong to us.
3 min read | Reflare Research Team
After the large-scale outbreak of WannaCry two months ago, this week saw another major ransomware outbreak initially targeting organizations in Ukraine but spreading globally. Since a large number of unsubstantiated rumours and sensationalized headlines have accompanied the malware, we will use this briefing to review the facts currently available.
Who, what and how?
The Petya malware appears to have initially targeted Ukrainian organizations by exploiting - among others - a vulnerability found in accounting software mandated to companies by the Ukrainian government. The use of this exploit indicates that the malware was at least partially targeted at Ukrainian organizations by its creators. Russian organizations appear to be affected strongly as well.
Who is behind the attack is unclear at the moment. While many rumours abound, we were unable to substantiate any of their claims.
How is Petya different from WannaCry?
The two ransomwares differ in three key ways:
1)Petya uses several different exploits to attack systems.
2)While WannaCry attempted to find new targets randomly on the internet, Petya appears designed to spread primarily within the local network that infected machines are connected to.
3)WannaCry encrypted the contents of files themselves. Petya encrypts the Master File Table of the hard disk partition. This process is significantly faster but chances for recovery are better.
Whether the creators of both ransomwares are the same or related is unknown at this point in time.
Nuclear Power Plants and other sensationalism
Several reports have stated that the Chernobyl nuclear power plant was hit by Petya. Similar headlines have stated that nuclear power plants in other countries were hit by the malware as well.
Upon further investigation, all of these incidents seem to boil down to a computer used in relation to the power plant having been compromised. The function of these computers is unclear, however, the exploits used by Petya lead us to assume that the computers were most likely used for clerical purposes.
None of the reactors has at this time reported an incident to their overseeing agencies. This indicates that the reactor itself was not affected.
Many news outlets and especially social media nonetheless jumped on the story, building on the trend of over-sensationalised commentary on the impact of this, and other recent security breaches. Please exercise caution when reading such reports. This caution should be taken further when discussing your organization’s security matters with senior leaders or stakeholders, as we see many senior decision makers who do not have a security background are poorly informed, or in some cases, outright wrong. To this point, claiming that a nuclear reactor was hacked because a regular personal computer related to it fell to ransomware is as ridiculous as claiming that a gun was hacked because the soldier carrying it lost his/her Facebook account to scammers.


